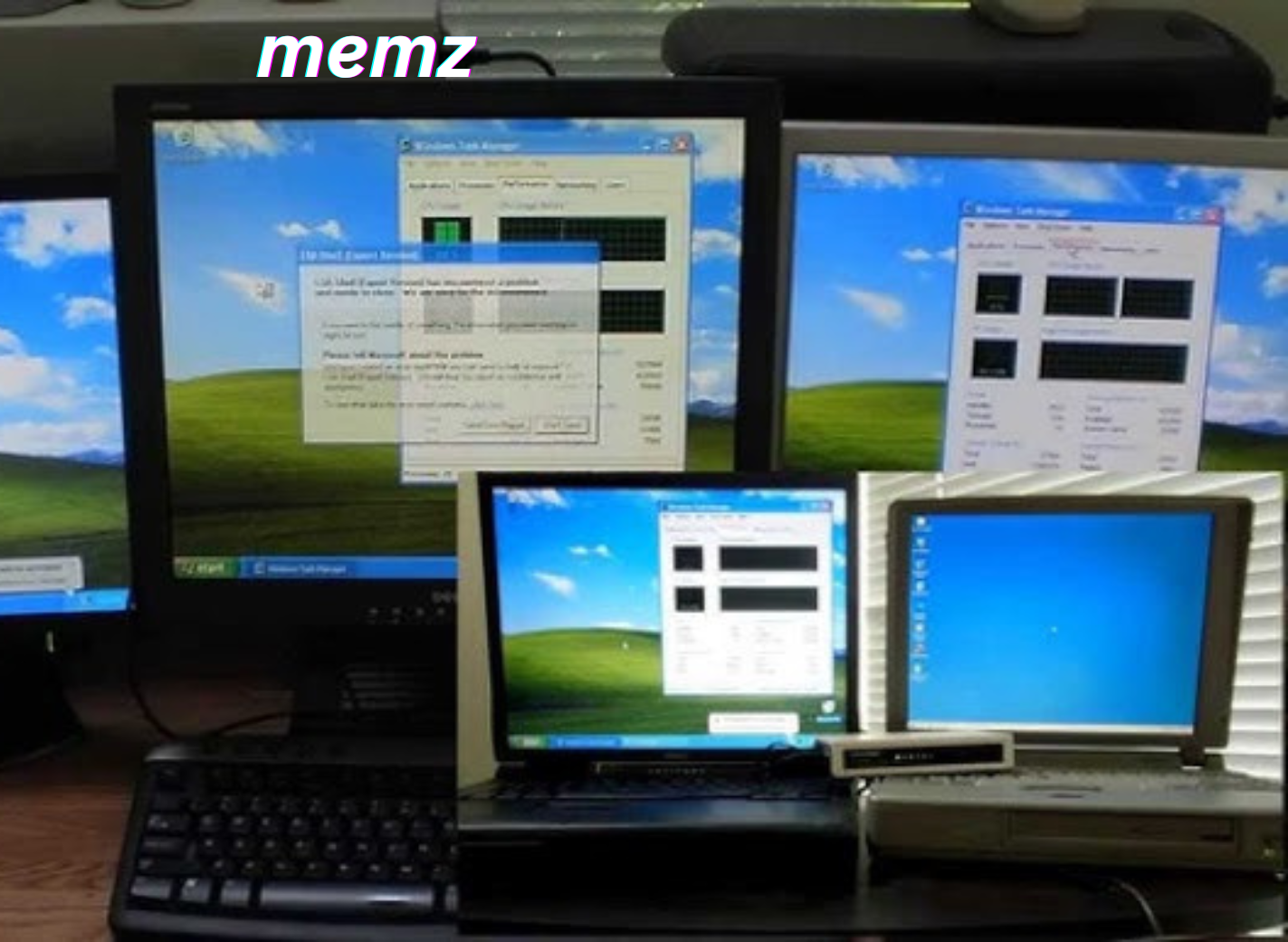
In the ever-evolving world of cybersecurity, few pieces of malware have captured the internet’s attention quite like the MEMZ virus. Unlike traditional malicious software designed solely for theft or destruction, MEMZ walks a bizarre line between chaos and memz creativity. Created as a joke, it gained viral fame for its theatrical, almost artistic approach to digital sabotage. MEYMZ doesn’t just crash your system—it does it with flair.
From dancing pop-ups and self-opening programs to a surreal Nyan Cat takeover of the boot sector, MEMZ has made a name for itself not by hiding in the shadows but by loudly announcing its presence. As such, it became more than a virus—it became a meme, a part of digital folklore, and a popular topic among tech enthusiasts, YouTubers, and curious users.
But despite its humorous facade, MEMZ serves as a potent reminder of the vulnerabilities we face in the digital age. It’s not just a quirky piece of software—it’s a compelling example of how easily curiosity and humor can turn into disaster if we aren’t careful with what we run on our machines. In this article, we’ll dive deep into the world of MEMZ: its origins, mechanics, impact, and how to protect against it.
The Origins of MEMZ From Joke to Digital Terror
The MEMZ virus was created in 2014 by a developer known online as Leurak. Originally crafted for YouTuber danooct1, known for testing and showcasing malware in controlled environments, MEMZ was never meant to be a real threat. It was a demonstration—a theatrical piece of code designed to entertain, not harm. However, the sheer creativity of its payloads and its spectacular display of chaos quickly made it an internet sensation.
MEMZ was released in two distinct versions: a harmless version intended for demonstration purposes, and a destructive version that could cause real and irreversible damage to a user’s system. The destructive variant, in particular, writes to the Master Boot Record (MBR), making the system unbootable after a restart. This blend of humor and real consequences is what set MEMZ apart from other joke viruses, earning it both praise for its creativity and criticism for its recklessness.
Over time, the MEMZ virus evolved from a one-off curiosity into a cultural icon in tech communities. Variants popped up with even more elaborate payloads, and online creators began incorporating it into reaction videos, tutorials, and digital forensics breakdowns. MEMZ wasn’t just a virus anymore—it was a phenomenon that sparked curiosity and debate among developers and cybersecurity experts alike.
Inside the Code How MEMZ Works
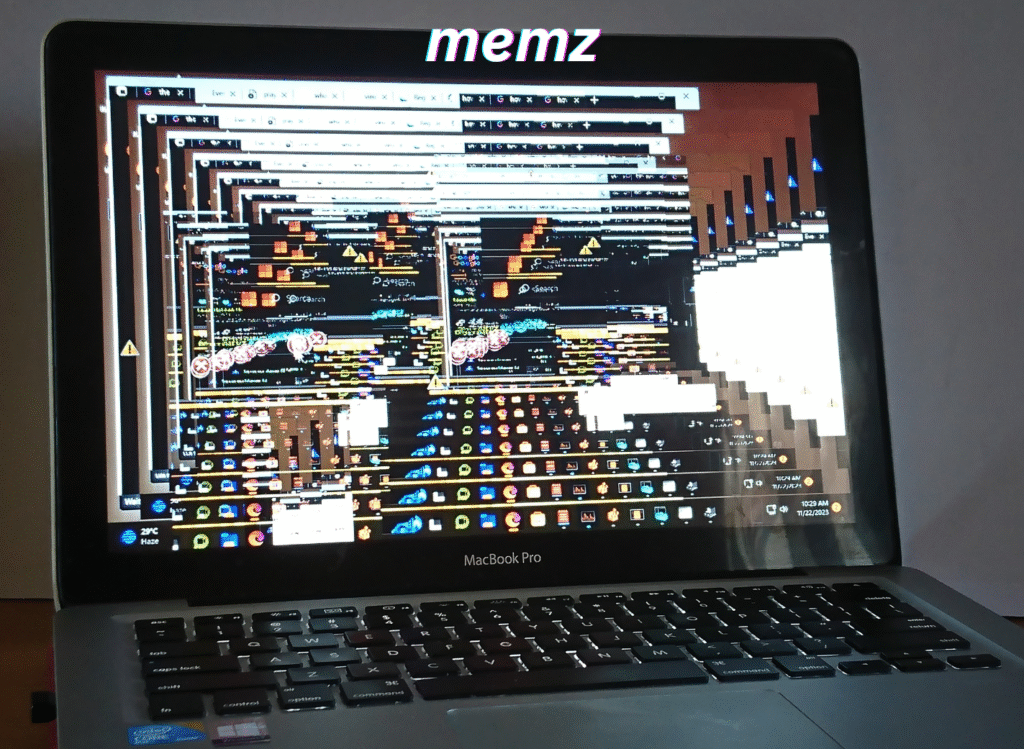
At its core, MEMZ is a Windows-based trojan, crafted in C++ and specifically designed to wreak havoc in the most visually chaotic way possible. What sets it apart from typical malware is that it doesn’t hide or remain stealthy—instead, it loudly and proudly announces its effects, immediately grabbing the user’s attention. MEMZ runs in stages, with each phase unleashing a more intense and bizarre set of payloads.
The infection begins the moment the executable is run. At first, seemingly minor glitches occur: the cursor starts moving on its own, windows open and close randomly, and text boxes appear filled with cryptic or humorous messages. As the virus progresses, it escalates into more extreme payloads such as keyboard inputs being scrambled, programs launching automatically, and recursive Notepad windows spamming gibberish on the screen.
One of the most iconic features of MEMZ is its final payload. Upon system restart—especially in the destructive version—the user is greeted not by their desktop, but by a custom bootloader that plays a distorted version of the Nyan Cat animation and song. This bootloader overwrites the MBR, making the machine unbootable without advanced recovery tools. This final act ensures that MEMZ doesn’t just disrupt a session—it ends it with an unforgettable bang, often requiring a full OS reinstall.
Consequences of Running MEMZ
Running MEMZ, especially the destructive version, has very real consequences. Unlike harmless malware that can be removed with antivirus software or system rollback, MEMZ alters critical system files and the Master Boot Record, leading to complete system failure. The payloads, while whimsical, are also designed to corrupt data, interfere with user inputs, and render the machine unusable after execution.
Once the virus is activated, users quickly find themselves overwhelmed. Programs open on their own, mouse movements become erratic, and visual glitches take over the screen. Attempting to close these pop-ups only results in more windows opening. The computer becomes a battleground of flashing icons, text boxes, and relentless interference. It becomes evident that the virus is beyond containment—the only endgame is total shutdown.
In some cases, users reported losing valuable data and being forced to completely reformat their systems. While some installed MEMZ in virtual machines or sandbox environments for fun, others mistakenly ran it on their main computers, unaware of its destructive potential. YouTube is filled with reaction videos of users watching helplessly as their machines succumb to the chaos of MEMZ. These testimonials are both hilarious and horrifying—an important lesson on what happens when entertainment collides with cybersecurity ignorance.
Prevention and Removal Can MEMZ Be Stopped
Preventing the MEMZ virus, like many forms of malware, comes down to awareness and responsible computing. Because it doesn’t propagate through networks or disguise itself like ransomware or spyware, users typically have to intentionally download and run it. That means MEMZ is largely a case study in social engineering and curiosity-driven risk. It often appears disguised as a funny game or hacker tool, luring users into executing it without understanding the consequences.
In terms of removal, things get complicated—especially with the destructive version. Once the Master Boot Record is overwritten, the system can’t start. Traditional antivirus programs like Windows Defender or Malwarebytes may detect and quarantine the file before execution, but once launched, they’re virtually useless. Recovery may involve booting into safe mode, using recovery media, or performing a complete OS reinstall—steps that are beyond the average user’s expertise.
The safest way to explore MEMZ is by running it in a virtual machine (VM) or sandboxed environment. This allows curious users to observe its effects without risking their actual systems. Many educational YouTube channels demonstrate MEMZ using these methods, turning the virus into a teaching tool rather than a threat. The key takeaway is simple: never run unknown executables on your primary machine, no matter how funny or intriguing they seem.
Conclusion
The MEMZ virus is a fascinating blend of art, code, and chaos. Originally created as a joke, it evolved into a legendary piece of malware—not for stealing data or spying on users, but for spectacularly destroying a system with creative flair. MEMZ is a modern parable for digital curiosity gone too far, showing how even “fun” software can have serious consequences.
What makes MEMZ stand out is not its technical sophistication, but its theatrical delivery and the cultural buzz it generated. From the quirky payloads to the unforgettable Nyan Cat finale, MEMZ serves as both a cybersecurity warning and a bizarre form of digital expression. Whether you view it as art, code, or cautionary tale, one thing is certain: MEMZ left a mark on the internet.
For anyone interested in exploring malware or computer security, MEMZ is a compelling case study. But remember—some digital doors, once opened, cannot be closed. Always test responsibly, educate others, and never underestimate the power of a so-called “joke virus.”
FAQs
Is MEMZ a real virus or just a prank?
MEMZ is both—a joke virus designed to cause chaos, but with very real and destructive consequences.
Can MEMZ be removed without reinstalling Windows?
Only if the destructive version hasn’t been run; otherwise, full OS reinstallation is often required.
What happens when you run MEMZ on a virtual machine?
It simulates all its chaotic behavior safely, making VMs ideal for testing MEMZ.
Is there a safe version of MEMZ to test for fun?
Yes, the non-destructive version omits the MBR overwrite and can be run in VMs for demonstration purposes.
Why does MEMZ use the Nyan Cat bootloader?
It adds a humorous, ironic twist to the virus’s destructive finale, reinforcing its meme-based origins.
You May Also Read: https://techbusinessus.com/strands-hint-today/